Digital.ai Deploy 22.1.x Release Notes
Digital.ai Deploy 22.1.1
Digital.ai Deploy 22.1.1 includes the following new features:
- OIDC Private Key authentication support
- Kubernetes Operator-based installer enhancements
- Plugin Manager enhancements
- Support for Microsoft Edge based on Chromium
- Version upgrades—supported databases
And more bug fixes and enhancements.
Support Policy
See Digital.ai Support Policy.
Upgrade Instructions
The Digital.ai Deploy upgrade process you use depends on the version from which you are upgrading, and the version to which you want to go.
For detailed instructions based on your upgrade scenario, refer to Upgrade Deploy.
Digital.ai Deploy 22.1.1 New Features
Here's what is new with Digital.ai Deploy 22.1.1.
Private Key JWT and Client Secret JWT Authentication Methods
- Digital.ai Deploy—22.1 and later—support
client_secret_jwtandprivate_key_jwtmethods to authenticate clients with OIDC-based ID providers such as Keycloak. - The JWT assertion must be digitally signed using a private key in asymmetric cryptography.
- Digital.ai Deploy—22.1 and later—support signed JWTs only—it does not extend to encrypted JWTs encoded in a JSON Web Encryption (JWE) structure.
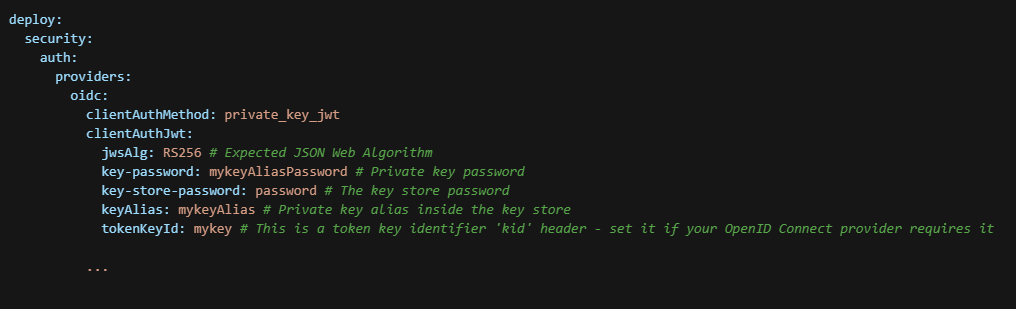
OIDC Private Key JWT Authentication
Digital.ai Deploy supports client authentication using the private_key_jwt method.
The following JSON Web Algorithms (JWA) are supported:
- RS256 (RSASSA-PKCS1-v1_5 using SHA-256)—this is the default if you use the private_key_jwt authentication method
- RS384 (RSASSA-PKCS1-v1_5 using SHA-384)
- RS512 (RSASSA-PKCS1-v1_5 using SHA-512)
- ES256 (ECDSA using P-256 and SHA-256)
- ES384 (ECDSA using P-384 and SHA-384)
- ES512 (ECDSA using P-521 and SHA-512)
- PS256 (RSASSA-PSS using SHA-256 and MGF1 with SHA-256)
- PS384 (RSASSA-PSS using SHA-384 and MGF1 with SHA-384)
- PS512 (RSASSA-PSS using SHA-512 and MGF1 with SHA-512)
Here's an example deploy-oidc.yaml file that uses the private_key_jwt authentication method.
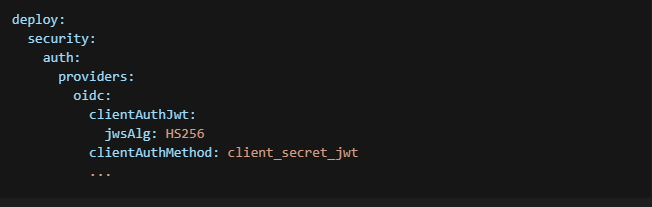
OIDC Client Secret JWT Authentication
Digital.ai Deploy supports client authentication using the client_secret_jwt method.
The following JSON Web Algorithms (JWA) are supported:
- HS256 (HMAC using SHA-256)—this is the default if you use the client_secret_jwt authentication method
- HS384 (HMAC using SHA-384)
- HS512 (HMAC using SHA-512)
You can configure the desired JWS algorithm using the deploy.security.auth.providers.oidc.clientAuthJwt.jwsAlg key.
Here's an example deploy-oidc.yaml file that uses the client_secret_jwt authentication method.
For more information, see Set Up the OpenID Connect (OIDC) Authentication for Deploy.
Kubernetes Operator-based Installer Enhancements
With Deploy 22.1.1, the Kubernetes Operator-based installer offers the following enhancements:
- Improvements to the installer to enhance stability
- Upgrade process improvements
- Uninstallation process improvements
- Keycloak is the default authentication manager when you log in to the Digital.ai Deploy interface.
- Central Configuration as a Standalone service is started by default when you install Digital.ai Deploy using Kubernetes Operator installer.
Plugin Manager Enhancements
With Deploy 22.1.1, you can now set the value of the -plugin-source flag when running the system as a service on Windows or Linux operating system. For more information, see Plugin Synchronization.
Support for Microsoft Edge Based on Chromium
Deploy 22.1 has been qualified to work with Microsoft Edge based on Chromium.
Version Upgrades—Supported Databases
Deploy 22.1 supports the following databases.
| Database | Versions Supported |
|---|---|
| PostgreSQL | 12.9, 13.5, and 14.2 |
| MySQL | 5.7 and 8.0 |
| Oracle | 12c and 19c |
| Microsoft SQL Server | 2017 and 2019 |
| DB2 | 11.1 and 11.5 |
Plugins and Integrations
Here's what's new with plugins and integrations.
-
AWS Plugin
-
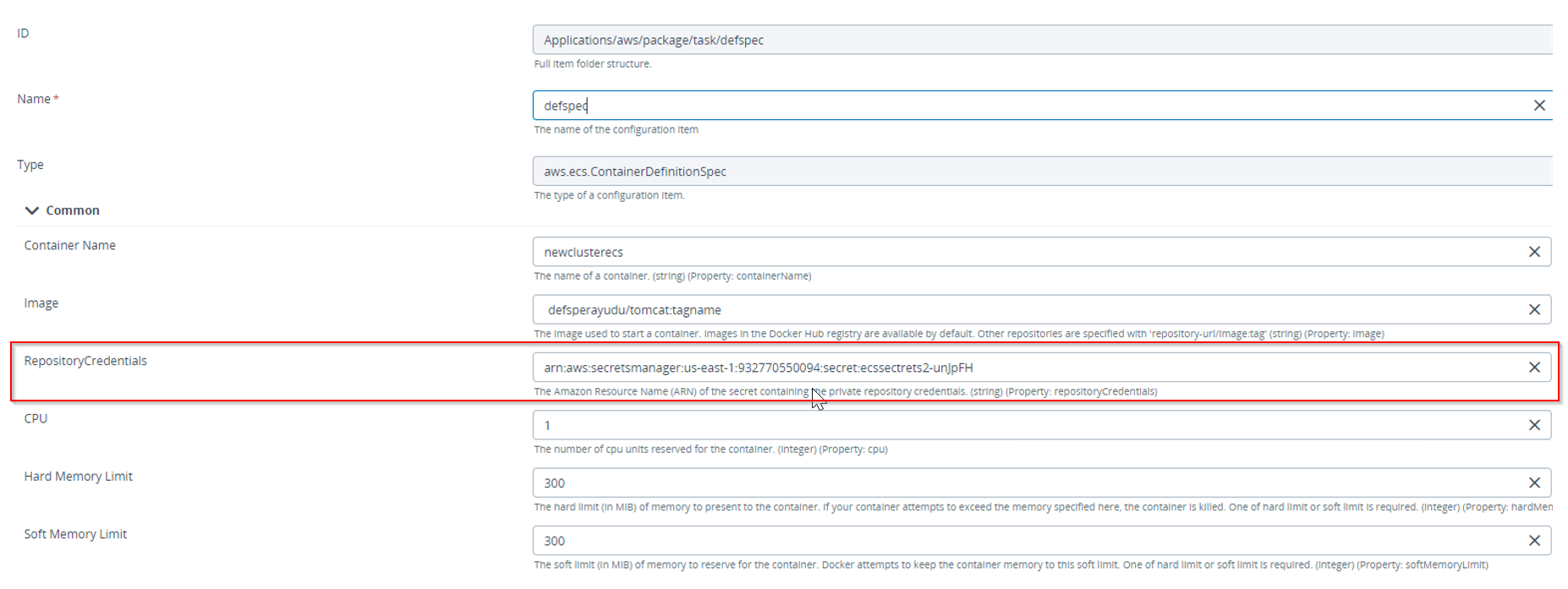
A new field, Repository Credentials has been added to pass the Amazon Resource Name (ARN) of the secret, which stores the private repository credentials.
-
Fixed the HTTPS proxy connection issue, which was throwing a connection failure.
-
Fixed dependencies for the UTC attribute not found issue.
-
Modified the ECS Service update strategy to update task revision rather than destroying and recreating it every time.
-
New parameters added for ECS service:
PidModeandIpcMode. -
New parameters added for ECS task:
dnsSearchDomains,dnsServers,entryPoint,startTimeout,stopTimeout,essential,hostname,pseudoTerminal,user,readonlyRootFilesystem,dockerLabels,healthCheck,environmentFiles,resourceRequirements,ulimits,secrets,extraHosts,systemControls, andlinuxParameters.
-
-
Azure Plugin
-
Fixed the HTTPS proxy connection issue, which was throwing a connection failure.
-
Fixed dependencies for the UTC attribute not found issue.
-
A new field, Application Settings has been added to add or modify the application settings in
azure.FunctionAppZip.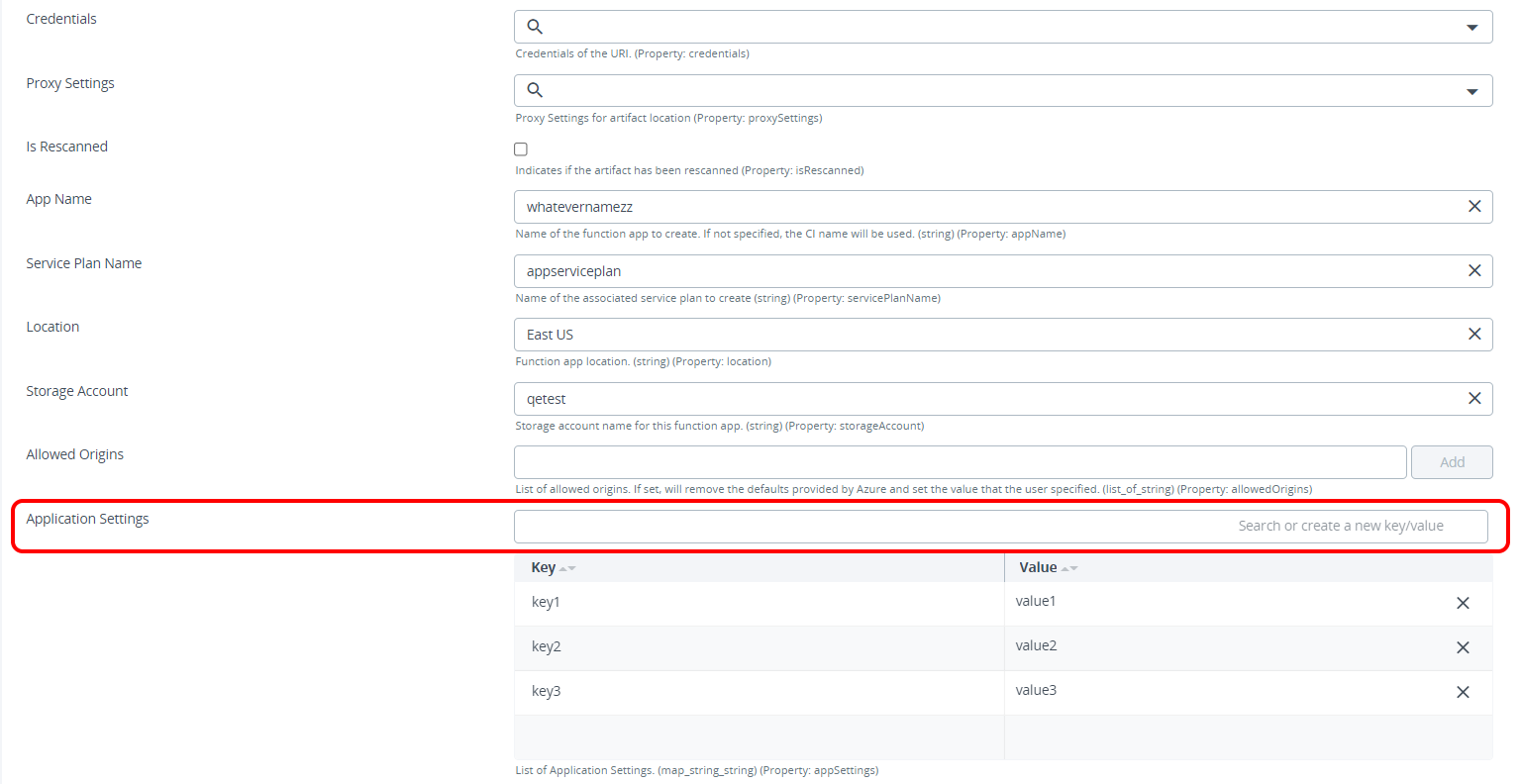
-
-
Docker Plugin
Fixed the HTTPS proxy connection issue, which was throwing a connection failure.
-
Internet Information Services Plugin
Fixed the issue, which was not removing the virtual directory from the IIS server.
-
Kubernetes Plugin
-
Fixed the HTTPS proxy connection issue, which was throwing a connection failure.
-
Fixed dependencies for the UTC attribute not found issue.
-
-
Terraform Plugin
Fixed the issue for the Terraform output variables, which were not captured for a remote backend.
-
Tomcat Plugin
Fixed the shell and batch scripts with validations for the start, stop, and status commands.
-
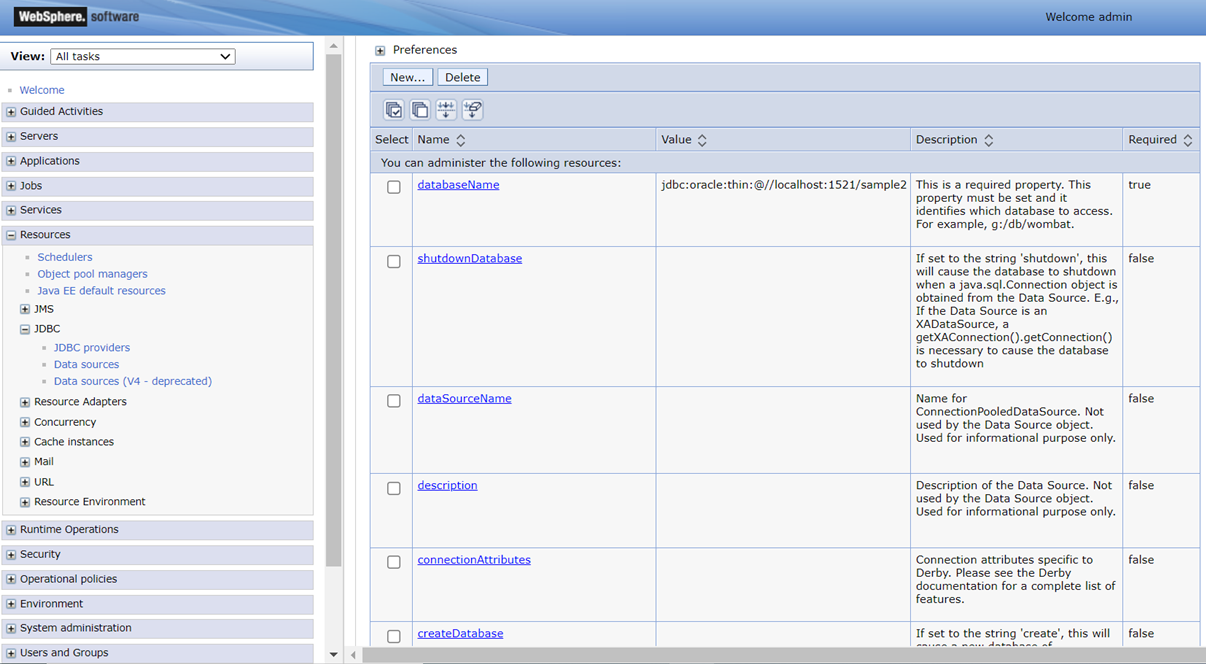
WebSphere Application Server Plugin
-
Creates datasource with default properties defined in WebSphere.
-
Fixed the issue with update of classloader order during a deployment update of
was.Earfile.
-
-
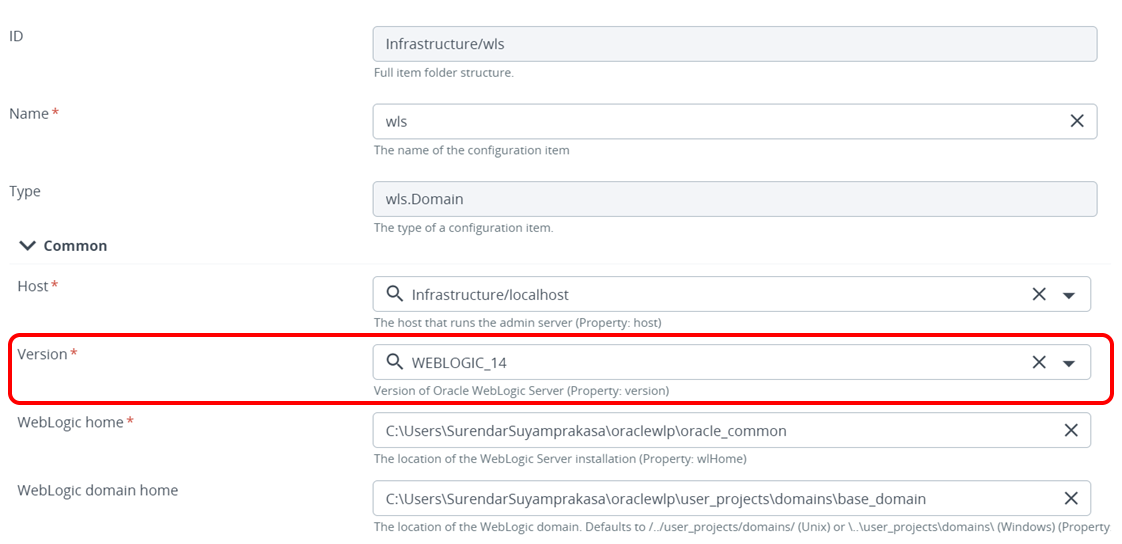
WebLogin Server Plugin
-
Supports Oracle WebLogic Server 14c.
-
Fixed the deployment order for side-by-side deployments. Note that, side-by-side deployment works only when a new version of the application is deployed next to an existing version.
-
Bug Fixes and Field Incidents
Bug Fixes and Field Incidents—22.1.1
- ENG-9219 - Fixed an issue that was displaying an error message while choosing the current month in the Date Range drop-down list of the Reports Dashboard section.
- ENG-5298 - Fixed an issue with the resolved placeholders that were not storing the values while deploying the
iis.WebContentto theoverthere.SmbHost. - ENG-9080 - Fixed an issue where the cluster data was not properly persisted in the database.
- FI-1022 - Fixed an issue that caused constant execution of
PermissionServiceAttachUpgradetask upon server restart. - FI-1011 - Fixed an issue that prevented the
Run.shcommand from starting the satellite with wrapper Java options. - FI-1006 - Fixed an issue that prevented the display of a particular activity in the monitoring and report pages.
- FI-982 - Fixed an issue that displayed an error in the Register Deployed section even after deployment was cancelled.
- FI-954 - Fixed a UI issue that prevented automatic user session timeouts past the threshold idle time.
- FI-953 - Fixed an issue that created a deployment task and indefinitely queued it when wrong hostname was entered for the
wls.Domaintype.
Bug Fixes and Field Incidents—22.1.2
- D-20597 - Fixed an issue with the Digital.ai Deploy Oracle Service Bus (OSB) plugin that prevented users from being able to deploy packages with placeholders.
- ENG-9087 - Fixed an issue with install-service.sh and install-service.bat by updating them to include the plugin-source=database flag.
- ENG-7906 - Fixed an issue due to which only users with Report-View permission were able to download the generated report.
- D-20598 - Fixed the INTERACTIVE_SUDO connection type vulnerability.
- D-20732 - Fixed a UI issue due to which the spinner was not displayed when you drag and drop the application and environment CIs to the deployment section.
Bug Fixes and Field Incidents—22.1.3
- D-18895 - Fixed an issue with the user session expiry for a deleted user, who has the permission or access to an active session. Now, a deleted user will be denied access to an active session.
- D-20538 - Fixed the deadlock issue within the Lock plugin.
- D-20452 - Fixed an issue with Deploy that is set up in HA mode, which shows a Null pointer exception while making changes in Instance customization.
- D-20857 - Fixed an issue with the permissions service REST API results, which were returning all configuration items instead of the folders.
Bug Fixes and Field Incidents—22.1.4
- D-18337 - Fixed a UI issue with the Resolved Placeholders table to show the lengthy Dictionary entries (with ellipses) fully when hovered over.
- D-19883 - Fixed an issue that removed the Digital.ai logo up on adding a custom logo.
- D-20191 - Fixed the Bad Request error (when roles were created) that occurred on sites with standalone Deploy permission service.
- D-21367 - Fixed a UI issue that prevented long Dictionary title from being shown in the Dictionaries section of the Environment view.
- D-21443 - Fixed an issue that caused deployments with long Dictionary title to error out.
Bug Fixes and Field Incidents—22.1.5
- D-21089 - If there are more than 1000 directories that don't inherit permission from their parent, then non-admin users will not be able to view any CIs. This issue is now fixed.
- D-21099 - Fixed a configuration issue in the export folder of Deploy.
- D-21492 - You cannot import applications with XLD CLI that has CI with file artifacts in an external repository. It is because the CI fails to authenticate with the repository. This issue is now fixed.