Digital.ai Deploy 22.2.x Release Notes
Digital.ai Deploy 22.2.0
Digital.ai Deploy 22.2.0 includes the following new features:
- Enable Profiling Logs for SQL Queries
- Operator-based installer—install Deploy in a Custom Namespace
- Additional parameters in OIDC configuration
- Downloadable Usage Summary Report
- Deployment API performance improvements
- Plugins and integrations
And more bug fixes and enhancements.
Support Policy
See Digital.ai Support Policy.
Upgrade Instructions
The Digital.ai Deploy upgrade process you use depends on the version from which you are upgrading, and the version to which you want to go.
For detailed instructions based on your upgrade scenario, refer to Upgrade Deploy.
Digital.ai Deploy 22.2.0 New Features
Here's what's new with Digital.ai Deploy 22.2.0.
Enable Profiling Logs for SQL Queries
-
Profiling can be enabled in Deploy which lets you log query details such as query parameters and time taken by a query to the
XL_DEPLOY_SERVER_HOME/log/profiling.logfile. -
The
XL_DEPLOY_SERVER_HOME/log/profiling.logfile is rotated the same way as other log files are.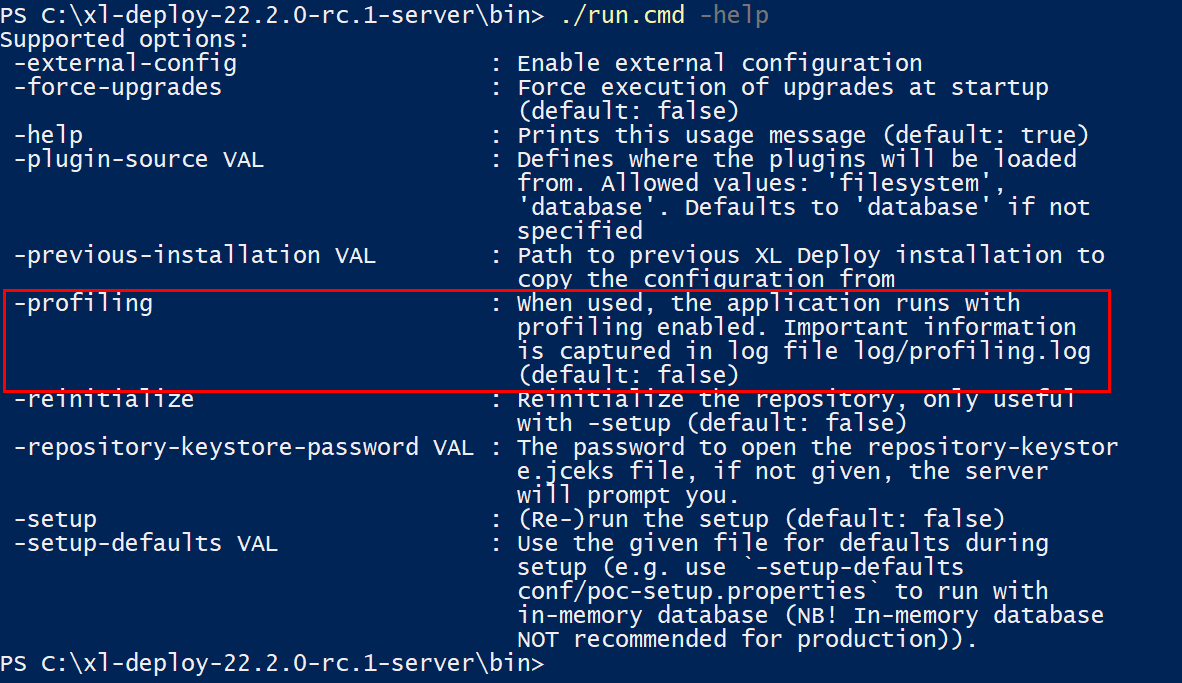
For more information, see Enable Profiling Logs for SQL Queries.
Operator-based installer—install Deploy in a Custom Namespace
Installing Digital.ai Deploy in a custom name space is one of the salient cloud-native features added to Digital.ai Deploy 22.2. You can now install Digital.ai Deploy in a custom namespace if:
- You would like to install multiple Deploy instances on the same cluster.
- You do not want to install Deploy in the default namespace: digitalai.
For more information, see: Install Deploy in a Custom Namespace.
Additional Parameters in OIDC Configuration
You can now send additional parameters to the OIDC provider as part of the OIDC authentication request.
Here's an example, in which you can find two additional parameters—param1 and param2.
deploy.security:
auth:
providers:
oidc:
clientId: "<Your client ID>"
clientSecret: "<Your client secret>"
clientAuthMethod: "<Your client authentication method here>"
issuer: "<Enter the Open ID Provider Issuer>"
keyRetrievalUri: "https://oidc.example.com/endpoint/keys"
accessTokenUri: "<The redirect URI to use for returning the access token>"
userAuthorizationUri: "<The authorize endpoint to request tokens or authorization codes via the browser>"
logoutUri: "<The logout endpoint to revoke token via the browser>"
redirectUri: "https://xl-deploy.example.com/login/external-login"
postLogoutRedirectUri: "https://xl-deploy.example.com/login/external-login"
idTokenJWSAlg: "<The ID token signature verification algorithm>"
rolesClaimName: "<Your roles claim>"
userNameClaimName: "<Your username claim>"
additionalParameters:
param1: false
param2: "str"
With such a configuration, the additional parameters are passed in the login URL as shown in the following example request URL.
https://example.oktapreview.com/oauth2/.../.../code_challenge=xyz¶m1=false¶m2=str
Downloadable Usage Summary Report
With Deploy 22.2, you can now download the usage summary report for a given time period in Excel format. For more information, see Download Usage Summary Reports.
Version Upgrades
Supported Databases
Deploy 22.2 supports the following databases.
| Database | Versions Supported |
|---|---|
| PostgreSQL | 13.6 and 14.2 |
| MySQL | 5.7 and 8.0 |
| Oracle | 12c and 19c |
| Microsoft SQL Server | 2017 and 2019 |
| DB2 | 11.1 and 11.5 |
Deployment API Performance Improvements
The Digital.ai Deploy 22.2 includes a series of performance improvements around deployment APIs.
Plugins and Integrations
Here's what's new and changed with plugins and integrations.
HashiCorp Vault Plugin
Introduced a new type of authentication called AppRole in the HashiCorp Vault plugin.
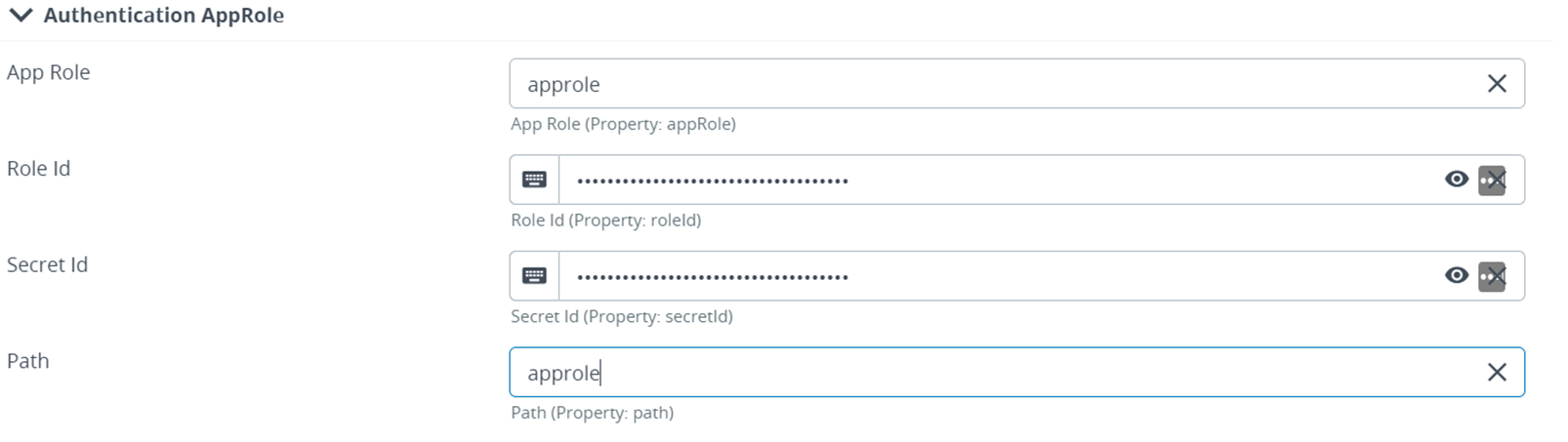
For more information, see Hashicorp vault
AWS Plugin
- Fixed the issue with the deployment target path in the S3 Bucket folder.
- Assume role with SSO/Temporary credentials is supported.
- Added missing parameters for ECS service and Task definition.
- ECS Service parameters:
ipcModeandpidMode - Task Definition parameters:
environmentFiles,resourceRequirements,ulimits,secrets,extraHosts,systemControls,linuxParameters,dnsSearchDomains,dnsServers,entryPoint,startTimeout,stopTimeout,essential,hostname,pseudoTerminal,user,readonlyRootFilesystem,dockerLabels, andhealthCheck
- ECS Service parameters:
For more information, see AWS
Kubernetes Plugin
Assume role with SSO/Temporary credentials is now supported by the Kuberbetes plugin.
Podman Plugin
With the Podman plugin, you can deploy Podman images to create containers. In addition, you can create network and volumes for these containers.
Here's a list of tasks supported by the Podman plugin:
- ContainerSpec
- NetworkSpec
- PodSpec
- VolumeSpec
- File/FolderSpec
For more information, see Podman
WAS Plugin
Fixed the data source creation failure issue in the WAS plugin by making changes to the condition of the admintask flow.
Tomcat Plugin
With the Tomcat plugin, the port field is now set to optional and control task scripts are updated.
Cloud Foundry Plugin
Fixed the connection error issue in the Cloud Foundry plugin by updating the Cloud Foundry SDK libraries.
Bug Fixes and Field Incidents
Bug Fixes and Field Incidents—22.2.0
- D-18895 - Fixed a user session expiry issue for deleted users. The user session of a deleted user expires as soon as you delete the user.
- D-18894 - Fixed an issue after which only users with the Report-View permission are able to download the generated report.
- D-20538 - Fixed the deadlock issue with the Lock plugin.
- D-20857 - Fixed an issue with the permissions service REST API results, which were returning all configuration items instead of the folders.
- D-18337 - Fixed a UI issue with the Resolved Placeholders table to show the lengthy Dictionary entries (with ellipses) fully when hovered over.
- D-21652 - Fixed the auto-refresh issue for newly created users that was occurring during CI creation and deployments.
- D-20191 - Fixed the Bad Request error (when roles were created) that occurred on sites with standalone Deploy permission service.
- D-20544 - Fixed the issue with the
lookup.SimpleLookupValueProviderConfiguration CI for the ssh check connection in theencryptedEntrieskey-value map. - D-20695 - Fixed the issue with the Invalid archive (jar file) that was not getting copied when Replace Placeholders option is enabled.
- D-21655 - Fixed the issue with the Digital.ai icon that was broken in the Registration page.
- D-21747 - Fixed the issue with the
active-user-sessions-enabled, which when set to false incentralConfiguration/deploy-server.yaml, is shutting down the server with an error. - D-19883 - Fixed an issue that removed the Digital.ai logo up on adding a custom logo.
- D-21347 - Fixed the issue with the Deploy server startup that was failing when the permission service is configured as standalone microservice.
- D-21448 - Fixed the issue with the connection leak in Active/Active HA setup.
Bug Fixes and Field Incidents—22.2.1
- D-21089 - If there are more than 1000 directories that don't inherit permission from their parent, then non-admin users will not be able to view any CIs. This issue is now fixed.
- D-21099 - Fixed a configuration issue in the export folder of Deploy.
- D-21492 - You cannot import applications with XLD CLI that has CI with file artifacts in an external repository. It is because the CI fails to authenticate with the repository. This issue is now fixed.
- D-21652 - Fixed the auto-refresh issue for newly created users that was occurring during CI creation and deployments.
- D-21742 - When you create a cluster with a managed server in WebSphere, it fails. This issue is now fixed.
- D-21745 - When you create a proxy-server cluster with a managed server in WebSphere, it fails. This issue is now fixed.